Author:
Max Wandera – CISSP, GLSC, Director of the Cybersecurity Center of Excellence at Eaton
Date
10/15/2018
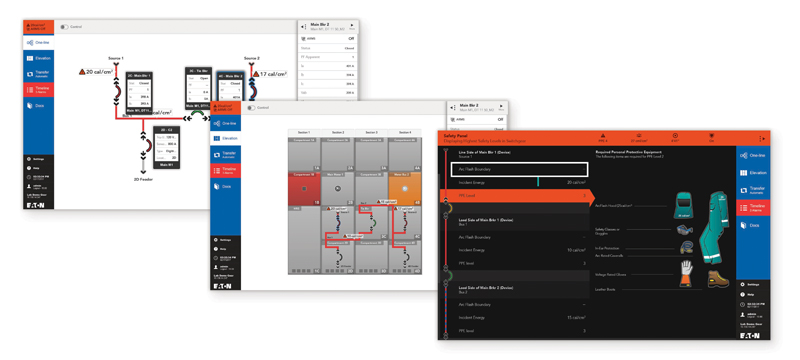
Figure 1. Eaton’s’ Power Xpert Dashboard is the first power management product certified to the UL 2900-2-2 Standard for cybersecurity. This user portal to Eaton’s switchgear enables customers to monitor, diagnose and control equipment from a location outside the arc flash boundary.
Last year, businesses were expected to spend an estimated $964 billion on IoT devices. (Source: Gartner) Moving forward, analysts forecast that connected devices and the data they generate will continue to grow exponentially. By 2020, an estimated 31 billion devices will be connected to the internet. (Source: IHS)
As customers deploy more intelligent and connected solutions, it is essential to trust and verify that the technologies they are relying on are designed, built and tested to proven engineering practices. For years, Eaton has maintained strict procedures at every stage of the product development process. The main goal of our approach to product security is to advance safety while protecting the availability, integrity and confidentiality of electrical systems.
Industry first cybersecurity collaboration with UL
We began collaborating with UL earlier last year to drive the development of new cybersecurity standards for power management products. Our mutual efforts are helping drive the development of common criteria for assessing products to ensure they meet industry standards and reduce cybersecurity risk. Through rigorous cybersecurity processes and having the first lab approved to participate in the UL Data Acceptance Program, we hope to set a precedent for developing products and systems that comply with the most stringent standards and expectations for safe, secure power management.
Further, our work with UL is helping establish measurable cybersecurity criteria for network-connected power management products and systems. As we introduce more intelligent and connected systems, this collaboration will continue to provide the industry with robust standards, testing methodologies and technologies designed to help device manufacturers build trust and verify claims supporting the highest level of defense against emerging cybersecurity threats.
5 critical steps to cybersecurity
The goal for manufacturers should be to ensure that products are compliant with cybersecurity standards and are secure when deployed in our customers’ environment by addressing risk from the beginning of the product development lifecycle. We address cybersecurity risks in products through a Secure Development LifeCycle (SDLC) with protocols in place that manage risks through threat modeling, requirements analysis, implementation, verification and ongoing maintenance —from inception to deployment and maintenance phases.
With continuously evolving system complexities, threat scenarios and technology, security is a continuous journey. We recommend the following five-step approach to support thorough risk mitigation throughout all phases of the device lifecycle process:
Click image to enlarge
Figure 2. Eaton manages cybersecurity risks in products through a Secure Development Lifecycle program. By way of threat modeling, requirements analysis, implementation, verification and ongoing maintenance, Eaton is managing risks through the entire product lifecycle. Image courtesy of Eaton.
1. Get to know the product requirements
Collect important background information from product teams to initially classify the product, whether the product to be built is a sensor, actuator, field device or system.
2. Learn how it’s built
There are a variety of products in the market, with countless components, interfaces and protocols. Review the architecture of the products in order to identify physical interfaces, protocols, data flows, deployment context and access scenarios. This can help set the stage for discovering where risks may hide.
3. See where the risk may lie
Methodically examine every facet of the product and create threat models to identify conceivable cybersecurity issues that may be a concern in the customer environment. With findings in hand, you can then finalize cybersecurity requirements.
4. Work to remove risk
Apply secure by design principal by ensuring cybersecurity is embedded in each phase of development – such as design, code reviews and product assessments – and correctly applied. Align findings with your framework requirements to confirm that you’re meeting the product’s cybersecurity goals. You should then document secure hardening and deployment guidelines according to industry best practices.
5. Confirm security
Validate requirements and findings from product assessments in order to help developers identify and fix any bugs discovered before developing a process to address any future vulnerabilities discovered in the field.
It is essential to recognize that cybersecurity, even when designed into technology, is dependent on how technology is applied as threats continue to evolve. For example, it is my responsibility to update my smartphone with manufacturer-provided updates. If I don’t make those updates, my device may be more vulnerable to attack compared to an updated device. Similarly, how a customer applies a technology and the updates and upgrades they decide to make in their systems and environment will impact cybersecurity in their applications.
As threats evolve, the industry should continue to identify where risk may lie, works to remove risk and offers updates to products regularly. An important part of the process is making sure that customers are aware of those upgrades and have trained resources to take advantage of the latest technologies and best practices available.
Eaton